Law Enforcement Battles Cyber Threats

[ad_1]
The United States Department of Homeland Security has published the results of its investigation into the teenage hacker group known as Lapsus$.
The report by the cyber safety review board (CSRB) found that a lack of government funding constrains law enforcement agencies. It also states that underreporting incidents further inhibits efforts to clamp down on cybercrime.
The Teenage Hacker Group That Attempted to Extort Microsoft and Nvidia
LapsusS rose to notoriety with a string of cyberattacks throughout 2022. The group’s first known target was the Brazilian Health Ministry, which had its computer systems compromised in December 2021.
Throughout 2022, LapsusS attacked a number of large technology firms, including Microsoft, Nvidia, Samsung, and Uber. Their tactics involve gaining access to private servers and then extorting victims with the threat of publishing or deleting their data.
In the UK, the group has become something of a media sensation due to the young age of some of its alleged core members.
As reported by the BBC at the time, seven teenagers were arrested under suspicion of being involved with the Lapsus$ hacks. Among them was the then 16-year-old Arion Kurtaj, who is alleged to be a leading figure within the group known by the pseudonym “White.”
In a trial that started last month, Kurtaj and an unnamed 17-year-old are accused of hacking systems belonging to Nvidia, Rockstar Games, Revolut, and Uber.
Despite Arrests, Cybersecurity Efforts Remain Hamstrung, Says CSRB
In its assessment of the threat posed by Lapsus$ and associated groups, the CSRB found that:
“Law enforcement remains underfunded for resource- and data-intensive investigations and disruptions against the full breadth of cyber threat actors.”
It also noted that “chronic underreporting” of cyber incidents hampers the government’s ability to warn other targeted entities, recommend mitigation measures, and seize stolen or extorted cryptocurrency and fiat money.
Crypto Central to Cyber Extortion
The CSRB report discusses cryptocurrency’s central role in cybercrimes such as the Lapsus$ hacks.
For example, it notes that hackers often demand ransom payments in crypto. Moreover, the darknet markets, where stolen data is typically sold, tend to utilize privacy coins for facilitating transactions.
However, the CSRB found no evidence that any of the firms targeted by Lapsus$ actually paid ransoms. The report adds that the FBI was unaware of Lapsus$ selling stolen data.
Considering this, the report typically presents Lapsus$ as a collective of crypto-savvy hackers.
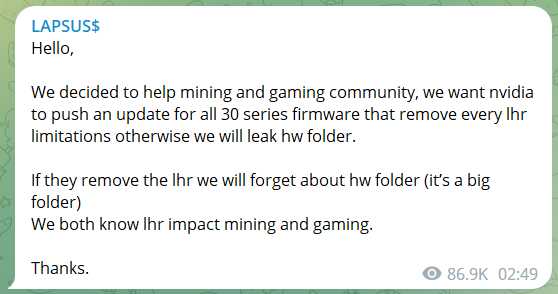
For example, it references an attempt by Lapsus$ members to extort Nvidia into updating its firmware in a way that would benefit Bitcoin miners. The hackers also offered to sell information that would allow miners to bypass hash rate limits imposed by Nvidia directly.
Recommendations From the Lapsus$ Report
As well as documenting Lapsus$ exploits, the CSRB makes a number of recommendations that could help prevent future hacks.
Many of these reiterate commonly acknowledged cybersecurity best practices. For example, the report suggests organizations transition toward passwordless verification and embrace more advanced multi-factor authentication techniques.
It also recommends the US government take a more proactive role in developing national cyber resilience. For example, it suggests ways the government could incentivize the adoption of more secure systems and procedures.
Finally, the CSRB advocates for a “whole-of-society” approach to threat mitigation.
The report notes that the juvenile status of Lapsus$ members complicated efforts to disrupt attacks. It recommends funding cybercrime prevention programs for young people to address this challenge.
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content.
[ad_2]
Source link
